Table of Contents
Stablecoin security is all about protecting these unique digital assets from the many tech and financial threats they face.Since they're designed to hold a steady value—usually pegged to something like the U.S. dollar—they've become a cornerstone of the digital economy. Keeping them safe is non-negotiable, because a failure in a major stablecoin can send shockwaves through the entire system.
Why Stablecoin Security Is the Bedrock of Digital Finance
It’s easy to think of stablecoins as just digital dollars, but that's selling them short. They're actually the fundamental rails that much of decentralized finance (DeFi) runs on. I like to think of them as the plumbing in a massive skyscraper—you don't see it, but if it breaks, the whole building grinds to a halt. The same is true here; if a major stablecoin fails, everything from lending protocols to global payment systems is immediately at risk.
This explosive growth has also painted a giant target on their backs. With so much money flowing through them, stablecoins are a magnet for attackers. A single vulnerability doesn't just put one asset in jeopardy; it can set off a chain reaction that hits trading, lending, and payments across the board. The stakes are incredibly high for everyone, from individual holders to the biggest financial institutions.
The Scale of the Risk
The stablecoin market has swelled to over $232 billion in circulation. While that growth has fueled a ton of innovation, it has also created massive security blind spots.
We saw a brutal real-world example of this with the catastrophic collapse of TerraUSD on May 12, 2022. It was a stark reminder of how quickly things can go wrong, wiping out a staggering $40 billion in market value almost overnight. That particular stablecoin was an "algorithmic" type, and it unraveled in a classic "death spiral" when mass withdrawals and a broken redemption mechanism sent it into freefall. It proved, in the most painful way possible, that even huge projects are fragile without rock-solid backing.
A stablecoin’s promise of stability is only as strong as its underlying security. A failure in reserves, smart contracts, or governance doesn’t just affect one asset—it erodes trust in the entire digital asset ecosystem.
Before we dive deeper into the specific threats and defenses, let's get a high-level view of the key areas we need to watch. The following table breaks down the core pillars of stablecoin security, giving you a quick reference for the concepts we'll be exploring throughout this guide.
Core Pillars of Stablecoin Security at a Glance
| Security Pillar | Primary Risk Area | Why It Matters for Stability |
|---|---|---|
| Collateral & Reserves | Insufficient or poorly managed backing assets. | If the assets backing the stablecoin are not there or lose value, the peg can break. |
| Smart Contracts | Code vulnerabilities, bugs, and exploits. | Flaws in the code can be exploited to drain funds or disrupt operations. |
| Algorithmic Stability | Flawed economic models and "death spirals." | The mechanism designed to maintain the peg can fail under market stress. |
| Oracles | Manipulation of external data feeds. | Inaccurate price data can trick the system, leading to incorrect liquidations or minting. |
| Custody | Theft or loss of collateral held by a third party. | The physical or digital security of the reserves is critical; a breach is catastrophic. |
| Governance | Centralized control and malicious protocol changes. | A compromised governance system can alter rules to benefit attackers or insiders. |
This table maps out our journey. Each of these pillars represents a potential point of failure, but also an opportunity to build a more resilient and trustworthy system.
A Critical Component of Digital Safety
Getting a handle on these vulnerabilities is the first real step toward building a safer financial future. It's helpful to see how stablecoin security fits into the broader field of Cyber Security, which gives us the foundational principles for protecting any digital system.
While the many benefits of stablecoins make them an essential tool for modern finance, their security can't just be an afterthought. Protecting these assets demands a deep, practical understanding of how they work, where they can break, and what we can do to safeguard them. That's exactly what this guide is for—we're going to build your expertise from the ground up.
Understanding How Different Stablecoins Work
Before we can really dig into stablecoin security, we have to get one thing straight: not all stablecoins are created equal. Far from it. Their core design—how they hold their value—is the single biggest factor determining their strengths, weaknesses, and where they might break under pressure.
Think of it like building a bridge. You can use steel cables, reinforced concrete, or even wood. Each material has different properties and can handle different kinds of stress. The same is true for the three main flavors of stablecoins.
This breakdown shows how stablecoins are built on a foundation of real-world assets, technology, and regulatory oversight.
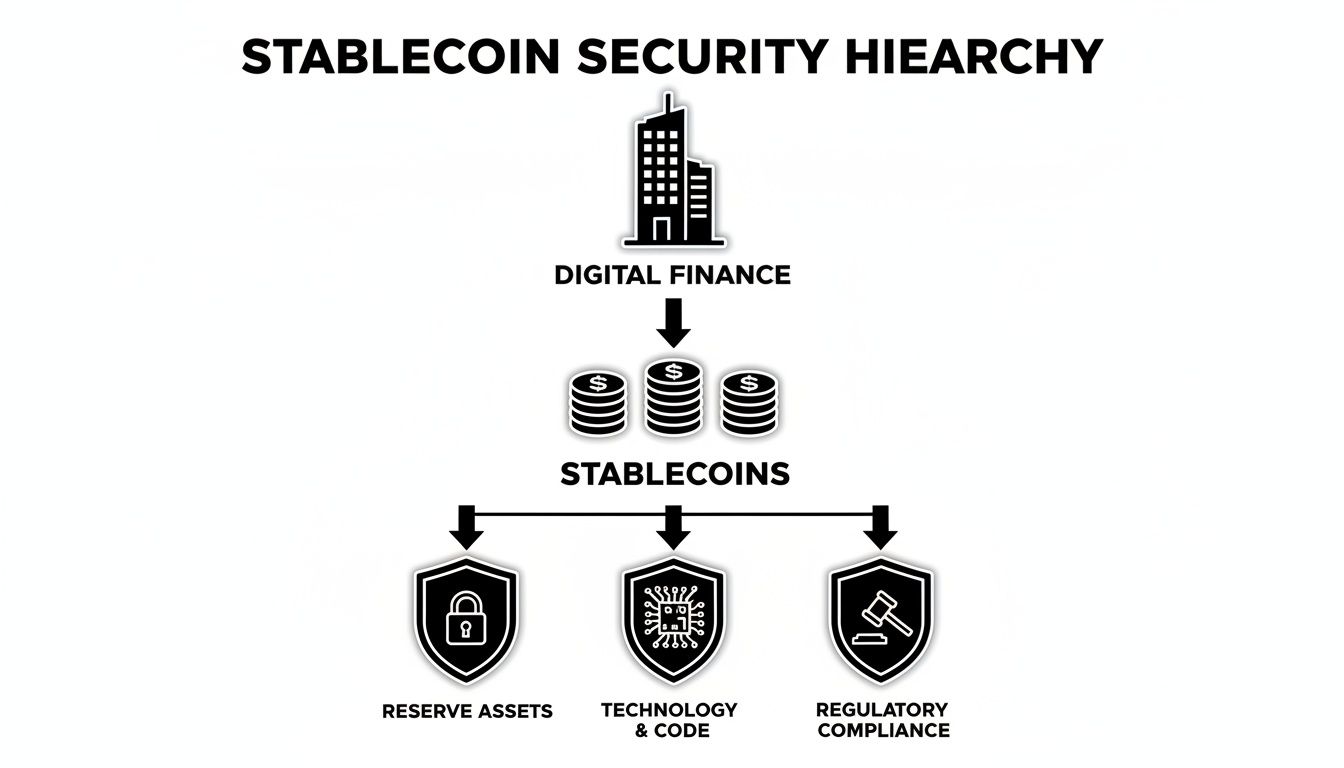
As you can see, a stablecoin is only as strong as the pillars holding it up: its reserve assets, the security of its code, and its ability to operate within the law.
Fiat-Collateralized Stablecoins
This is the most common and easiest-to-understand model out there. For every single stablecoin token in circulation, there's a corresponding real-world dollar (or other fiat currency) sitting in a bank account or invested in super-safe assets like U.S. Treasury bills.
It’s basically a digital IOU. When you buy a token like USDC or USDT, you're handing a dollar to the issuer, and they give you a digital claim check. Anyone holding that claim check can, in theory, go back to the issuer and redeem it for the real dollar.
The security of this whole setup boils down to one simple thing: trust. You have to trust the company behind the coin to actually have the money they say they have and to manage it responsibly.
- Biggest Worry: Custodial risk. Since all the money is held in a central pot, it's a huge target for theft, mismanagement, or even government seizure.
- How We Check: Regular audits and reserve attestations from major accounting firms are non-negotiable. Without them, users are essentially just taking the issuer's word for it.
Crypto-Collateralized Stablecoins
These stablecoins swap out dollars for other cryptocurrencies, like Ethereum, to back their value. But because crypto is notoriously volatile, you can't just back a dollar with a dollar's worth of ETH. It would be a recipe for disaster.
Instead, they rely on over-collateralization.
Think of it as a crypto pawn shop. To mint, say, $100 worth of a stablecoin like DAI, you might need to lock up $150 worth of ETH in a smart contract. That extra $50 is a safety buffer. If the price of ETH starts to fall, the system can automatically sell off your collateral before it's worth less than the stablecoin you minted, protecting the peg.
The big win here is decentralization—no single company controls the vault. But that introduces a whole new set of technological landmines.
The stability of the entire system hangs on the flawless execution of its smart contracts and the integrity of its price feeds (known as oracles). One tiny bug in the code or a manipulated price feed can bring the whole thing crashing down.
Algorithmic Stablecoins
Here’s where things get really complex—and, historically, really fragile. Algorithmic stablecoins have no collateral backing them at all. Zero.
Instead, they use a sophisticated set of algorithms and smart contracts to constantly manage the token supply, aiming to keep the price pegged at $1.
Imagine a central bank run entirely by code. When the price of the stablecoin dips below $1, the algorithm creates incentives for people to buy it, pushing the price back up. When it goes above $1, it incentivizes selling. It's a delicate, automated dance of economic theory and financial engineering.
While brilliant on paper, this model has a terrible track record in the real world. The spectacular collapse of TerraUSD (UST) is the poster child for what happens when these systems face real market panic. They can enter a "death spiral"—a vicious feedback loop where falling prices trigger more selling, which causes prices to fall even faster, until the algorithm simply can't keep up and the peg shatters completely.
The core risk is the model itself. It’s only as strong as the economic assumptions baked into its code. To learn more about the specific mechanisms at play, check out our deep dive on how stablecoins work.
Mapping the Stablecoin Threat Landscape
Knowing the different types of stablecoins is one thing, but truly understanding their security means digging into where things can go wrong. The stablecoin security landscape is a minefield, with threats lurking in the code, the collateral, and even the human processes that tie it all together. You have to think like an attacker mapping out a fortress—every potential vulnerability is a hidden gate or a weak spot in the wall.
Attackers don't just see a single asset. They see a complex machine full of moving parts, where a failure in one area can set off a domino effect across the entire system. Let's break down these threat vectors one by one so you can get a real-world feel for what can go wrong and, more importantly, learn to spot the red flags.

Smart Contract Exploits
At the very heart of decentralized stablecoins and the DeFi protocols they power are smart contracts. This self-executing code is what makes everything run without a middleman, but it’s also a huge point of failure. One bug or logic flaw in the code, and an attacker can drain millions in the blink of an eye.
This isn't just theory. We saw it happen with the July 2023 Curve Finance exploit, which put hundreds of millions in stablecoin liquidity on the line, all because of a vulnerability in its smart contracts. These attackers are always on the hunt for common flaws like:
- Reentrancy Bugs: This classic exploit lets an attacker repeatedly call a function within a single transaction, tricking the contract into sending them far more money than they're entitled to.
- Logic Errors: Sometimes it's just a simple coding mistake. Under the right conditions, these errors can cause the contract to behave in unexpected ways, often leading to massive, unintended fund transfers.
- Poor Access Controls: This is like leaving the admin password on a sticky note. Flaws here can let unauthorized users take control, minting new tokens out of thin air or changing the system's most critical rules.
Oracle Manipulation and Price Attacks
Many stablecoins, especially the crypto-collateralized ones, lean heavily on external data feeds called oracles to get the real-time price of their collateral. The system needs this price to know when a user's position is under-collateralized and needs to be liquidated to protect the peg. This reliance on outside information creates a prime target for attack.
If an attacker can manipulate the price an oracle is feeding into the protocol, they can trick the system into making catastrophic mistakes. A flash loan attack is the weapon of choice here.
Here's the playbook:
- The attacker borrows a huge sum of money—we're talking millions—using a flash loan. They don't need collateral, but they have to pay it back in the same transaction.
- They use this massive pile of cash to manipulate the price of a collateral asset on a decentralized exchange, specifically one the oracle is watching.
- The oracle, none the wiser, reports this fake, inflated price back to the stablecoin protocol.
- Acting on this bad data, the protocol lets the attacker do serious damage, like borrowing perfectly good stablecoins against now-worthless collateral or triggering improper liquidations that the attacker profits from.
This entire sequence unfolds in a matter of seconds. It's a surgical strike against the protocol's window to the real world, turning its own security rules against itself.
Stablecoin security isn't just about what's happening inside the code; it's about making sure the information coming from the outside is trustworthy. A manipulated oracle can turn a perfectly secure smart contract into a ticking time bomb.
Custody and Centralization Risks
When you look at fiat-backed giants like USDC and USDT, the biggest threat isn't a clever hack on the blockchain. It's the real-world custody of their reserves. These companies are sitting on billions of dollars in actual bank accounts and other traditional assets. While that sounds simple, it creates a massive, centralized point of failure.
This introduces custodial risk—the very real danger that the assets backing the stablecoin get mismanaged, stolen, or even seized. A successful cyberattack on the issuer’s internal systems could compromise those reserves or, even worse, give hackers the keys to mint unauthorized tokens, instantly wrecking the stablecoin's value.
On top of that, these issuers are centralized companies, making them subject to government and regulatory pressure. A government order could freeze their assets or shut down their operations, leaving holders around the world unable to redeem their tokens. When you use these stablecoins, you’re placing your trust in the issuer's operational security and their ability to navigate a complex legal world. This is just one of many factors to weigh when you're looking at the broader landscape of potential stablecoin risks.
Governance Attacks
Many decentralized protocols operate like a democracy, where token holders vote on everything from smart contract upgrades to managing the treasury. It's a powerful model, but it’s not foolproof.
In a governance attack, a bad actor accumulates enough governance tokens to seize control of the voting process. Once they have a majority, they can pass malicious proposals designed to enrich themselves at everyone else's expense. Think of it as a hostile takeover at the protocol level. They could vote to drain the treasury, change collateral rules to favor their own positions, or even write a backdoor into the code for a future exploit. They use the system’s own rules to tear down its defenses from the inside out.
Learning From The Wreckage: What Stablecoin Failures Teach Us
Theory can only take you so far. To really understand stablecoin security, you have to look at the battlefield—the major failures that have shaped the industry. These aren't just stories; they're detailed blueprints of what happens when a design flaw or a security oversight meets the real world. Modern security practices weren't dreamed up in a lab; they were forged in the fire of these disasters.
The crypto world, unfortunately, provides plenty of harsh lessons. Hacks and exploits are a constant threat. In fact, roughly $2.2 billion has already been stolen this year, a sharp 21% jump from 2023. These high-profile attacks, often stemming from something as fundamental as a compromised private key, are a brutal reminder of the financial devastation that follows a breach.
The Terra/UST Collapse: A House of Cards
When people talk about stablecoin disasters, the first name that comes to mind is almost always TerraUSD (UST). Its collapse in May 2022 was a seismic event. UST was an algorithmic stablecoin, which means it wasn't backed by dollars in a bank. Instead, it was supposed to hold its $1 peg through a clever, automated relationship with its sister token, LUNA.
On paper, it looked like a brilliant piece of financial engineering. In reality, it was a time bomb. The moment the market got spooked and large-scale withdrawals began, the entire mechanism shattered.
At its heart, the system had a fatal, reflexive flaw. When people rushed to sell their UST, the algorithm desperately minted more and more LUNA to absorb the shock. This flooded the market, cratered LUNA's price, and created the infamous "death spiral." A falling LUNA price made people even less confident in UST, leading to more selling, which meant more LUNA had to be minted. The whole thing fed on itself until it was worth nothing.
The implosion vaporized over $40 billion in value and sent shockwaves through the entire crypto market. The lessons learned were painful but clear:
- Purely algorithmic stability is a myth. Models that rely only on incentives and code can completely break down under the pressure of real human panic.
- Collateral isn't a suggestion; it's a necessity. Without a real-world anchor, there's nothing to stop the freefall when the balancing act fails.
- Trust is everything. Once the market loses faith that $1 is truly $1, a bank run is almost impossible to stop, no matter how clever the algorithm is.
When The Stablecoin Is Safe, But The Venue Isn't
Sometimes, the stablecoin itself is perfectly sound, but the DeFi platforms it lives on are not. This is a huge, often overlooked, part of the security puzzle. The attack on the Ronin Network in March 2022 is a perfect case study. Hackers made off with over $625 million, a huge chunk of which was in USDC stablecoins.
Here, the attackers didn't crack the stablecoin's code. They broke the bridge connecting it to other blockchains.
The hackers managed to get their hands on the private keys for the network's validator nodes—the gatekeepers that approve transactions. By controlling a majority of these keys, they could sign off on their own fraudulent withdrawals, draining the network's funds. From the stablecoin issuer's point of view, the transactions looked completely legitimate. There was nothing they could do to stop it.
This incident shows that your security is only as strong as the weakest link in the chain. It’s not just about the stablecoin issuer; it’s about every protocol, bridge, and smart contract you interact with. Even seemingly contained glitches, like the bug that briefly created a $300 trillion stablecoin ghost for Paxos, prove how interconnected systems can lead to bizarre and dangerous results.
To really grasp the different ways things can go wrong, it helps to compare these major incidents side-by-side.
Incident Analysis of Key Stablecoin Failures
| Incident | Stablecoin Type | Primary Vulnerability | Key Takeaway |
|---|---|---|---|
| Terra/UST Collapse | Algorithmic | "Death spiral" from a reflexive, undercollateralized design. | Algorithmic models without hard asset backing are exceptionally fragile under market stress. |
| Ronin Network Hack | Fiat-Collateralized (USDC) | Compromised private keys on a cross-chain bridge. | A stablecoin's security is dependent on the ecosystem it operates within, not just its own design. |
| Beanstalk Farms Exploit | Algorithmic | Governance attack via a flash loan. | On-chain governance itself can be an attack vector if not properly secured against economic exploits. |
| Iron Finance Collapse | Algorithmic (Partial) | Bank run triggered by a flawed redemption mechanism. | Even partially collateralized models can fail if the algorithmic component creates a feedback loop of panic. |
These post-mortems aren't just history lessons. They are essential reading for anyone trying to build, use, or invest in stablecoins, showing exactly where the fault lines lie.
Actionable Security Practices for Everyone Involved
Knowing the threats is one thing; actively defending against them is another entirely. This is where we move from theory to practice. Real stablecoin security isn't about finding a single silver bullet—it's about a shared responsibility where everyone, from the individual holding a few dollars to the issuer managing billions, plays a part.
Think of it as layers of defense. By taking these steps, each group can add a crucial layer of protection, strengthening the entire stablecoin ecosystem against the vulnerabilities we've discussed.

Security Checklist for Investors and Holders
As a user, you are the ultimate guardian of your own assets. Your personal security habits are the most important line of defense.
Verify Reserve Reports Diligently: Don't just take an issuer's word for it. Actively seek out regular, third-party attestations from reputable accounting firms. Go a step further and look at the composition of those reserves. Are they backed by cash and safe government securities, or riskier, less liquid assets?
Diversify Your Holdings: It's the oldest rule in the book for a reason. Avoid concentrating all your funds into a single stablecoin, no matter how solid it seems. Spreading your capital across two or three different, well-backed stablecoins can save you from a catastrophic loss if one of them fails.
Prioritize Secure Self-Custody: If you're holding a meaningful amount, get it off the exchange. A hardware wallet gives you sole control over your private keys, insulating you from exchange hacks, freezes, or collapses. For a deeper dive into this vital practice, check out our guide on storing stablecoins securely.
Scrutinize Smart Contract Interactions: Before you click "approve" on any DeFi transaction, pause. Triple-check the contract address you're interacting with and the specific permissions you're granting. A single click on a malicious dApp can give it the power to drain your wallet.
Best Practices for Developers and Builders
Developers are the architects of this new financial world. The code they ship underpins the security of the billions in stablecoins flowing through DeFi, making their practices absolutely critical.
Adhere to Secure Coding Standards: This is non-negotiable. Follow battle-tested patterns for smart contract development (like checks-effects-interactions) to shut down common attack vectors like reentrancy. Always use well-audited and widely trusted libraries from groups like OpenZeppelin.
Mandate Multiple Third-Party Audits: A single audit isn't enough. Before deploying any code that will handle user funds, get it reviewed by at least two independent and respected security firms. An audit isn't a magic guarantee, but it’s an essential filter for catching vulnerabilities before they get exploited.
Integrate Real-Time Threat Monitoring: Don't just ship it and forget it. Implement tools that watch for suspicious on-chain activity 24/7. Automated alerts for huge transactions or interactions with known scammer addresses can give your team the precious minutes needed to respond to an attack in progress.
Essential Guidelines for Stablecoin Issuers
Issuers are the bedrock of the entire system. They hold the ultimate responsibility for maintaining the trust and stability that gives a stablecoin its value. For them, security and transparency aren't just good ideas—they're everything.
For an issuer, transparency is not a feature; it is the product. Every decision, from reserve management to governance, must be conducted with the assumption that it will be scrutinized by millions of users and regulators.
To live up to this standard, issuers must obsess over three core pillars:
Radical Reserve Transparency: Publish daily, professionally audited proof-of-reserves. These reports must offer a granular breakdown of the backing assets, proving they are liquid, low-risk, and held in segregated accounts that are protected from company bankruptcy.
Robust Governance and Key Management: Eliminate single points of failure. All critical operations—minting, burning, and moving reserve funds—must be protected by multi-signature controls. This makes it exponentially harder for an insider threat or a single stolen key to cause a disaster.
Proactive Regulatory Engagement: Don't wait for the regulators to knock. Work with them to build clear compliance frameworks. This not only protects the project legally but also builds immense confidence with institutional users who demand regulatory clarity.
How Regulation Is Shaping Stablecoin Security
Technical safeguards are only one side of the coin. True stablecoin security ultimately depends on a solid legal and regulatory foundation. As stablecoins ballooned into a market worth hundreds of billions, governments and financial watchdogs have understandably stopped watching from the sidelines.
They’re now actively stepping in to set clear rules for the road. This shift from a "wild west" atmosphere to a regulated one is all about protecting consumers and maintaining broader financial stability. For stablecoin issuers, this means security and transparency are no longer just good ideas—they are fast becoming legal mandates. That regulatory pressure is a powerful catalyst, pushing the entire industry toward much higher standards.
The Rise of Comprehensive Frameworks
We're starting to see landmark regulations emerge that provide a real blueprint for how to run a stablecoin operation safely. Europe’s Markets in Crypto-Assets (MiCA) regulation is a perfect example, setting strict requirements for issuers that fundamentally strengthen security.
These new rules aren't just suggestions; they mandate specific actions that tackle historical weak points head-on:
- Reserve Transparency: Issuers are now required to maintain sufficient, highly liquid reserves and publish regular, audited reports. This simple rule makes it infinitely harder to operate a stablecoin without proper backing.
- Operational Resilience: Companies must prove they have robust internal controls and risk management frameworks in place. This helps prevent everything from operational blunders to internal fraud.
- Investor Protections: Clear rules on redemption rights guarantee that holders can actually swap their stablecoins for fiat currency when they want to. This prevents a crisis where users are left holding suddenly worthless tokens.
By transforming "should-dos" into "must-dos," regulation forces a level of discipline that code alone cannot. It provides a legal backstop for the technical promises of stability, building the institutional trust needed for mainstream adoption.
The Importance of Proof of Reserves
A huge piece of this regulatory push is the formalization of Proof of Reserves. This isn't just about an issuer publishing a blog post saying, "we have the money." It's a rigorous verification process carried out by independent, reputable auditing firms.
These attestations confirm that an issuer holds high-quality, liquid assets that are equal to or greater than the value of all the stablecoins they've issued. For users and institutions, these reports are an indispensable part of due diligence. They offer clear, third-party validation that a stablecoin is backed exactly as it claims. As regulatory frameworks mature, these attestations are becoming the gold standard for separating well-managed projects from the riskier, more opaque ones.
Common Questions About Stablecoin Security
Diving into stablecoins can feel complex, and it’s natural to have questions about keeping your money safe. When we talk about stablecoin security, it’s crucial to get straight answers. Let's tackle some of the most frequent questions people ask.
Are Fiat-Backed Stablecoins Completely Safe?
Nothing in finance is ever completely risk-free, and stablecoins are no exception. Fiat-backed stablecoins are often seen as the most secure type, but that security isn't guaranteed. It all comes down to trusting the company that issues them.
You’re essentially betting that the issuer has 1:1 reserves in a bank, that those reserves are easy to access, and that the company can handle everything from a bank run to regulatory pressure. That's a lot of trust.
So, how do you verify? Always look for their latest reserve reports from well-known auditing firms. If an issuer isn't transparent or their reports are infrequent, that's a serious red flag.
What's the Biggest Risk With Decentralized Stablecoins?
For decentralized stablecoins, the number one threat is smart contract vulnerability. These platforms run entirely on code, and a single bug or clever exploit can be disastrous. Think of it like a bank vault with a hidden flaw in its design—once discovered, it can be emptied in minutes.
Another major weak point is their reliance on oracles, which feed them real-world price data. If an attacker can manipulate that data feed, they can trick the protocol into making catastrophic decisions. This isn't just a theory; it's a tactic that has been used to drain millions from DeFi platforms.
The core promise of a decentralized stablecoin is only as strong as its code. Thorough, repeated security audits are not optional; they are a fundamental requirement for user safety and long-term viability.
Can a Stablecoin Lose Its Peg?
Absolutely. It happens more than you might think. A "de-peg" is when a stablecoin's price breaks away from its $1 target. Sometimes it's a temporary blip caused by wild market swings, but other times it's a permanent failure.
The dramatic collapse of TerraUSD is the textbook example of a permanent de-peg. But even the most respected stablecoins can wobble, briefly trading for $0.99 or lower during a market panic or when confidence in the issuer gets shaky. It's a stark reminder to always understand the mechanics keeping your stablecoin stable.
At Stablecoin Insider, we provide the in-depth analysis and up-to-the-minute news you need to stay ahead in the digital asset space. Explore our expert coverage to make smarter, more secure decisions at https://stablecoininsider.com.






