Table of Contents
Institutional crypto custody is a whole different ball game from the crypto wallet you might have on your phone. We're talking about specialized services designed to securely store and manage massive digital asset portfolios for big players—think hedge funds, asset managers, and major corporations.
This isn't just about holding crypto; it's about providing a fortress of security, ensuring regulatory compliance, and offering the kind of operational support needed when billions of dollars are on the line.
Understanding Institutional Crypto Custody
For an individual, a hardware wallet or a mobile app might be perfectly fine for managing their crypto. But for an institution? That's a non-starter. The stakes are astronomically higher. We're dealing with client funds, fiduciary responsibilities, and a maze of regulatory requirements.
Institutional crypto custody was born to fill this massive gap. It provides the bedrock of trust and security that large, traditional financial players need before they'll even consider dipping their toes into the digital asset market.
A good way to think about it is comparing a personal safe in your closet to a bank's deep vault system. Your home safe is great for your own valuables, but the bank's vault is a completely different beast. It has multi-layered security, armored transport, ironclad access protocols, and hefty insurance policies. It's built from the ground up to integrate high-value assets into a regulated financial system.
Why Standard Wallets Just Don't Cut It
A standard crypto wallet, whether it's software or hardware, simply isn't built for the unique pressures of an institutional setting. Here’s where they fall short:
- Single Point of Failure: Most consumer wallets are tied to a single private key or seed phrase. If that gets lost, stolen, or compromised, the assets are gone. Poof. Forever.
- No Real Operational Controls: They can’t handle things like multi-user access, tiered approval workflows for transactions, or the detailed audit trails that compliance officers demand.
- Serious Regulatory Gaps: Critically, they don't meet the legal definition of a "qualified custodian," which is a deal-breaker for many investment funds that are legally required to use one.
Institutional custody solves these problems by creating a secure, compliant, and operationally sound framework for managing digital assets at scale. It’s the essential bridge connecting traditional finance with the world of crypto.
The Ever-Changing Regulatory Environment
The regulatory scene is one of the biggest forces shaping the institutional custody space. A recent game-changer was the repeal of the SEC's Staff Accounting Bulletin 121 (SAB 121).
This rule used to force financial institutions to list clients' crypto holdings as liabilities on their own balance sheets. This was a huge headache, as it tied up massive amounts of capital and pretty much scared most banks away from offering custody services. With SAB 121 gone, that barrier has been lowered, opening the door for many more traditional players to get involved.
This dynamic environment makes it more crucial than ever for firms to understand the different digital asset custody solutions available. Choosing the right one is key to entering the space safely and setting up for success.
A Look at Core Custody Models and Technologies
When an institution decides to hold digital assets, the first question isn't just "which wallet?" It's a much deeper question about architecture. How you store crypto assets defines everything: your security, how you access your funds, and whether you can meet your compliance obligations. At the heart of it all is a fundamental trade-off between having direct control versus delegating that responsibility to an expert.
This fork in the road leads to two main paths: self-custody and third-party custody.
With self-custody, you’re the master of your own domain. The institution holds its own private keys, giving it complete autonomy. The flip side? The entire weight of security, creating bulletproof operational procedures, and managing the underlying technology rests squarely on your shoulders. It’s a heavy lift.
Most institutions opt for third-party custody. This means handing over the assets to a specialized, and usually regulated, provider. This move outsources the enormous technical and security headaches to a firm that does this for a living, which is why it's the go-to choice for fiduciaries and any organization with strict regulatory standards to meet.
The Storage Spectrum: Hot, Warm, and Cold Wallets
No matter which custody model you choose, your assets will live in different environments depending on how quickly you need to access them. It helps to think of it just like a bank manages its cash.
Hot Wallets: These are like the cash in a bank teller's drawer. They're connected to the internet, ready for immediate transactions like funding a trading account or processing a client withdrawal. That constant connectivity makes them incredibly convenient but also the most exposed to online threats.
Cold Wallets: This is the bank's main vault, deep underground and completely offline. Assets in "cold storage" are kept on devices that have zero connection to any network—a technique called an "air gap." It offers the highest level of security against hackers, but getting funds out is a much slower, more deliberate process.
Warm Wallets: This is the middle ground, offering a smart blend of security and speed. Think of it as the smaller, day-safe in the back office. It might be on a secure, private network with heavy access controls, making transactions faster than from the deep vault but far more protected than the teller's drawer.
To give you a clearer picture, this table breaks down the key differences between these storage solutions.
Comparison of Crypto Custody Storage Solutions
| Storage Type | Connectivity | Security Level | Access Speed | Primary Use Case |
|---|---|---|---|---|
| Hot Storage | Always online | Lower | Instant | Daily trading, frequent payments, DeFi interactions |
| Warm Storage | Online or on-demand on private networks | Medium | Minutes to hours | Rebalancing, operational reserves, scheduled settlements |
| Cold Storage | Completely offline ("air-gapped") | Highest | Hours to days | Long-term holdings, strategic reserves, inheritance |
As you can see, a sophisticated institutional setup doesn't just pick one; it uses a mix of all three to balance daily operational needs with the paramount requirement for robust security.
The diagram below shows how all these pieces—security, regulation, and operations—come together to form a complete institutional custody framework. It’s not about a single piece of tech; it's about building a fortress.
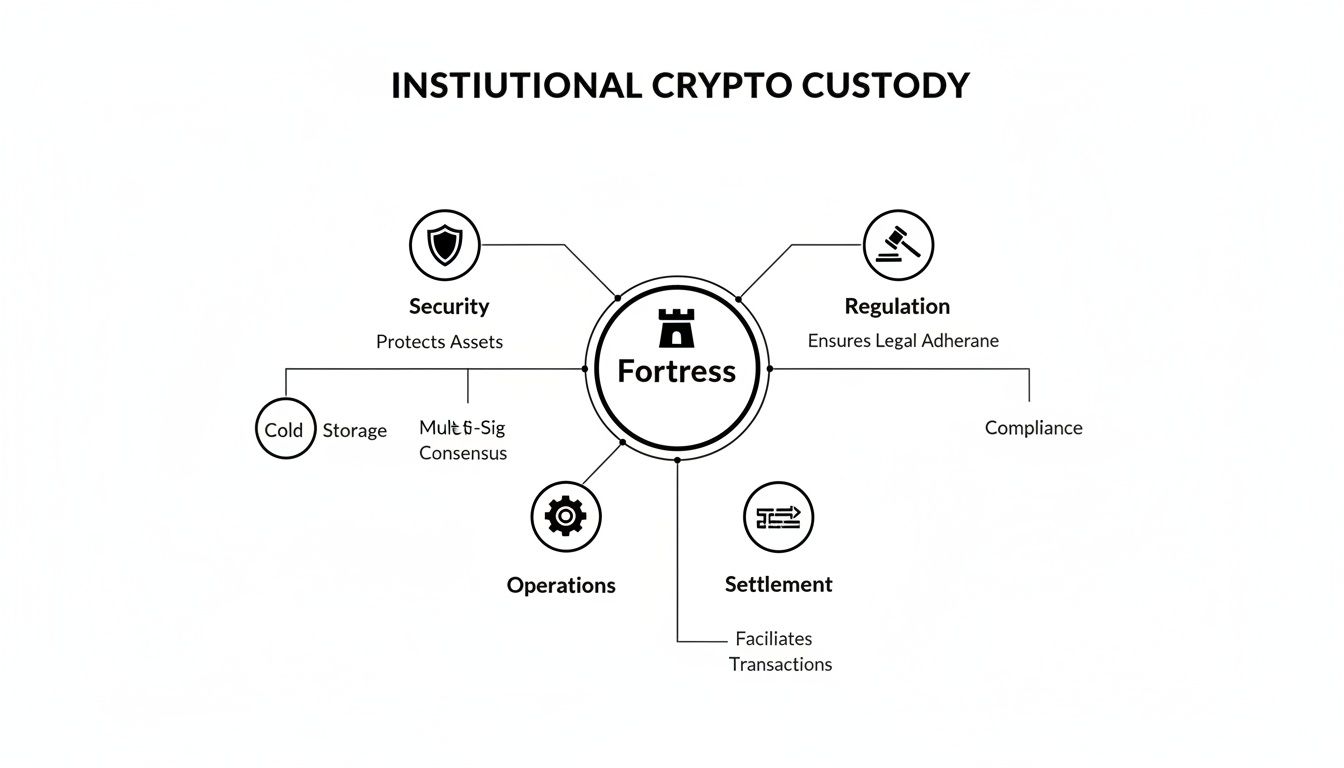
Advanced Tech That Kills Single Points of Failure
The nightmare scenario for any custodian is a single private key falling into the wrong hands. To eliminate that risk, institutional crypto custody now relies on some seriously advanced cryptography. The two most important technologies in the game today are Multi-Party Computation (MPC) and Hardware Security Modules (HSMs).
Multi-Party Computation (MPC) is a game-changer. It’s a cryptographic technique that ensures a complete private key never exists in one place, ever. Instead, the key is mathematically split into multiple encrypted "shards" that are distributed across different systems, servers, or even individuals. To sign a transaction, these shards work together to produce a valid signature without ever being reassembled into a whole key. This means a thief would have to breach multiple, isolated systems at the exact same time to get control—a monumentally difficult task.
MPC flips the script on key management. Instead of a single, vulnerable secret you have to defend, you get a distributed, resilient security system where the whole is far greater than the sum of its parts.
Hardware Security Modules (HSMs) add a layer of physical, Fort Knox-level security. These are specialized, tamper-resistant devices built for one purpose: to safeguard cryptographic keys. You can generate and store keys inside an HSM, but you can never extract them. If the device detects any attempt at physical tampering, it will instantly wipe itself clean. HSMs are the gold standard for protecting the key shards used in an MPC setup or for securing the master keys in a cold storage array.
When you combine MPC and HSMs, you get a defense-in-depth strategy that’s incredibly powerful. Each MPC key shard can be stored within its own HSM, layering cryptographic distribution with physical security. This powerful combination is what enables firms like Fireblocks to build secure infrastructure for major payment processors. To see this in action, you can explore how MoneyGram integrates Fireblocks for stablecoin settlements. It's a perfect real-world example of how this advanced security model allows even the most complex digital asset operations to run smoothly and securely.
The Pillars of Custody Security and Protection
When we talk about institutional crypto custody, we're really talking about building a digital Fort Knox. While clever cryptography like MPC and HSMs are the building blocks, genuine security is a multi-layered game. It's a blend of technology, iron-clad procedures, and independent verification designed to safeguard billions in assets from every imaginable threat.
This means you need comprehensive cybersecurity strategies woven into every part of the operation. You have to assume an attack can come from anywhere, so your defenses must be everywhere.

The Technical Backbone of Security
The central principle of institutional-grade protection is simple: eliminate any single point of failure. This isn't achieved with one magic bullet, but through a combination of powerful technologies working together to make a successful breach next to impossible.
Air-Gapped Systems for Deep Cold Storage
The ultimate security blanket is the air gap. This means physically isolating the storage devices from any network connection—no Wi-Fi, no ethernet, nothing. Private keys held in these systems have never touched the internet, making them completely immune to online hacking. This is the gold standard for holding strategic, long-term reserves.
Defense-in-Depth Architecture
A "defense-in-depth" strategy is all about layers. Think of a medieval castle: it has a moat, high walls, watchtowers, and armored guards. If an attacker gets past one, another is waiting. In the digital world, this looks like:
- Hardware Security Modules (HSMs): Specialized, tamper-resistant hardware built for one job: protecting cryptographic keys.
- Multi-Party Computation (MPC): A cryptographic method that splits a single private key into multiple encrypted "shards." The full key never exists in one place at any time, foiling theft.
- Network Security: The basics done right—firewalls, intrusion detection systems, and constant penetration testing to find weaknesses before attackers do.
This layered approach ensures that if one defense fails, several others are ready to stop an attack in its tracks. These are foundational concepts for asset protection, which we also cover in our guide to https://stablecoininsider.org/stablecoin-security/.
The Human Element: Operational Protocols
Technology is only half the battle. The most sophisticated systems can be brought down by a simple human mistake or a malicious insider. This is why strict, repeatable operational protocols are just as critical as the tech itself.
These protocols are the rulebook. They govern every single action taken within the custody environment.
A custodian's true strength is measured not just by its firewalls but by its operational discipline. Every transaction, every policy change, and every user action must be governed by strict, enforceable rules that leave no room for error.
Key operational controls you'll see include:
- Multi-User Approvals: This prevents a single rogue employee from moving funds. It's often called an "m-of-n" policy, where a certain number of approvals are needed (e.g., 3 out of 5 executives must sign off on a transaction).
- Address Whitelisting: Assets can only be sent to pre-approved, verified wallet addresses. Even if an account is compromised, this stops an attacker from draining funds to their own wallet.
- Time-Locked Withdrawals: A mandatory waiting period is enforced between the time a withdrawal is requested and when it's actually executed. This delay creates a vital window to spot and cancel any fraudulent activity.
The Gold Standard of Verification: SOC Attestations
So, how does an institution really know a custodian is doing all this? You can't just take their word for it. The answer is independent audits, and in this world, SOC 1 and SOC 2 reports are the industry benchmarks.
These reports are prepared by third-party auditors who comb through every detail of a custodian's internal controls.
- SOC 1: Focuses on controls that could impact a client's financial statements.
- SOC 2: Evaluates controls against key principles: security, availability, processing integrity, confidentiality, and privacy.
Getting a clean SOC report is a grueling and expensive process. For an institution, it’s non-negotiable. It provides verifiable, third-party proof that a custodian's security and operational controls are not just talk—they’re real, tested, and effective. It's a cornerstone of due diligence and provides genuine peace of mind.
Navigating the Regulatory and Compliance Landscape
Institutional crypto custody doesn't exist in a vacuum. It’s deeply embedded in a complex and constantly changing legal environment. For any serious financial player, getting a handle on this regulatory maze isn't just good practice—it's a fundamental requirement for staying in business. These rules exist to protect investors, stamp out illicit activity, and ultimately, maintain the stability of the entire financial system.
Think of the regulatory structure as the invisible architecture supporting the whole institutional crypto ecosystem. Before you can build a solid custody strategy, you have to understand this foundation, which is a web of government agencies, licensing requirements, and continuous reporting duties.
Key Regulators and the Qualified Custodian Rule
In the United States, a handful of powerful bodies call the shots when it comes to institutional crypto custody. Their roles can sometimes overlap, which creates a pretty intricate compliance puzzle for institutions to solve.
Securities and Exchange Commission (SEC): The SEC’s main job is investor protection, and its "Qualified Custodian" rule is a big deal. The rule basically says that investment advisers have to keep their clients' funds with a designated institution, like a regulated bank or trust company, that meets a very high bar.
Office of the Comptroller of the Currency (OCC): As part of the U.S. Treasury, the OCC is in charge of all national banks. Their guidance was a game-changer because it officially gave federally chartered banks the green light to offer crypto custody services.
New York Department of Financial Services (NYDFS): Anyone in the crypto space knows about the NYDFS and its tough "BitLicense" framework. Earning a charter from them is widely seen as a gold standard in regulatory approval, signaling top-tier operational integrity.
For most asset managers and funds, using a qualified custodian isn't really a choice; it's a legal mandate. This designation is critical because it assures everyone that the custodian has the necessary net worth, operational controls, and asset segregation practices to protect client funds, even if the custodian itself runs into trouble.
The Foundation of Compliance: KYC and AML
Beyond getting the right licenses, day-to-day compliance really boils down to two core pillars: Know Your Customer (KYC) and Anti-Money Laundering (AML). These aren't just one-time checkboxes. They are active, ongoing processes that have to be woven into the very fabric of a custodian's platform.
KYC is all about verifying a client's identity to make sure they are who they claim to be. AML takes it a step further by actively monitoring transactions for any suspicious activity tied to money laundering or terrorist financing. The best custodians use sophisticated blockchain analytics tools to trace where funds came from and flag any assets that might be tainted by illicit activity. Our in-depth article on digital asset compliance dives much deeper into these crucial processes.
Compliance is the bedrock of trust in institutional finance. Without robust KYC and AML procedures, a custodian cannot protect its clients or itself from the significant legal, financial, and reputational risks present in the digital asset space.
The recent spot Bitcoin ETF boom is a perfect illustration of how this works in the real world. Those ETFs pulled in a staggering $32 billion in net inflows, a feat made possible only because they rely on regulated custodians like Coinbase Custody and Fidelity Digital Assets. This wave of institutional confidence was built on the back of evolving SEC standards for custody, which helped calm earlier fears about risk and safety.
Insurance and Risk Mitigation: The Final Layer
Even with world-class security and airtight compliance, you need one last layer of protection: insurance. Institutional-grade insurance policies are designed specifically to cover losses from theft, whether it's an external hack or an inside job. These policies, often backed by major global insurers, provide a crucial financial safety net.
But you have to read the fine print. Coverage limits, what’s excluded, and how assets in hot versus cold storage are treated can differ dramatically from one policy to the next. A strong insurance policy is the ultimate backstop, giving institutions and their clients peace of mind that their assets are protected even in a worst-case scenario. It’s also important to look beyond general rules and find specific guidance on addressing crypto liquidity risks to ensure you’re fully covered.
Integrating Custody into Your Business Operations

Think of modern institutional crypto custody as much more than just a digital vault. It's really an operational hub—the secure bridge connecting an institution's digital assets to its day-to-day business. This is how static holdings are put to work and become productive capital.
The magic behind this connection is the Application Programming Interface, or API. APIs are what let different software systems talk to each other, creating smooth, automated workflows. A custodian's API is essentially a secure command center, giving a business the power to manage its assets programmatically without ever cutting corners on security.
Connecting Custody with Core Financial Tools
With a solid API, a custodian can plug directly into the essential software that a financial institution relies on every day. This weaves digital assets into the company's broader financial strategy, breaking them out of their isolated silo.
The most common integrations include:
- Trading Desks and Execution Venues: You can move assets from deep cold storage to a trading account to act on market opportunities, all without manual fuss.
- Portfolio Management Systems: These systems get fed real-time data on custodied holdings, which means portfolio tracking, valuation, and risk analysis are always up-to-date.
- Treasury Management Systems (TMS): This allows a corporate treasurer to view and manage digital assets right alongside traditional cash and securities, simplifying reporting and liquidity planning.
This kind of integration is a game-changer. Imagine a hedge fund setting up automated rules to rebalance its portfolio. When a certain price target is hit, an API call automatically moves assets from secure custody to an exchange. The process is fast, secure, and removes the risk of human error.
The Central Role of Custody in the Stablecoin Economy
Custodians are the bedrock of the entire stablecoin ecosystem. They provide the trust and infrastructure that allows stablecoins to operate on a global scale. From the moment a stablecoin is minted to its use in payments, a custodian is involved.
A qualified custodian handles several critical jobs:
- Issuance and Redemption: They hold the actual fiat reserves (like U.S. dollars) backing the stablecoin, offering transparent, auditable proof that the money is really there.
- Attestation and Reporting: Custodians team up with auditors to produce regular attestations, which verify that every single stablecoin in circulation is fully backed by assets in their care.
- Secure Treasury Management: They protect the reserve assets from theft or loss, which is what ensures a stablecoin holds its peg and its issuer stays solvent.
Without the security, transparency, and regulatory alignment provided by institutional custodians, the multi-billion dollar stablecoin market simply could not exist. They are the trusted third parties that make a trustless system viable for mainstream finance.
Real-World Applications and Workflows
This deep integration opens the door to some powerful new ways for institutions to operate. For a corporation, it means treating assets like Bitcoin as part of its treasury strategy—much like MicroStrategy does. They can use their custodied crypto to hedge against inflation or even as collateral for financing.
Financial firms are using custody to safely tap into DeFi protocols, earning yield on assets without ever directly handling private keys. They can also manage tokenized securities that represent real-world assets like real estate or equity on the blockchain. The possibilities just keep growing as the technology matures, and the ability to link these assets to payment gateways via a crypto payment API is quickly becoming a must-have for global commerce.
How to Choose an Institutional Custody Partner
Picking the right partner for institutional crypto custody is one of the most critical decisions your firm will ever make. This isn't just about finding a place to store digital assets; it's about forming a foundational partnership. You’re entrusting a provider with the keys to the kingdom, so their security, compliance, and operational chops have to be absolutely bulletproof.
To get this right, you need a methodical approach that cuts through the marketing noise and gets to the heart of what matters. Think of it less like choosing a vendor and more like conducting a deep-dive operational risk assessment. If you don't vet every single pillar of their business, you're leaving a door open for a catastrophic failure.
Security and Technology Assessment
Your first stop, always, is their security architecture. A custodian’s entire reason for being is to keep assets safe, so their defenses need to be fortress-like. Don’t just accept their claims at face value—you have to get your hands dirty and dig into the nitty-gritty of their security model.
Here’s what you should be drilling down on:
- Key Management: How exactly are private keys born, stored, and used? Is their system built on Multi-Party Computation (MPC), Hardware Security Modules (HSMs), or some combination of the two? Get the specifics.
- Storage Policies: Ask for the exact split. What percentage of assets are kept in truly air-gapped cold storage versus online "hot" wallets? More importantly, what are the ironclad procedures for moving funds between them?
- Third-Party Audits: Demand to see the paperwork. Can they show you recent SOC 1 and SOC 2 reports? What about independent penetration test results that verify their security controls actually work under pressure?
A custodian that gets cagey about their security stack is waving a giant red flag. The best, most reputable providers are proud of their defenses and will welcome the intense scrutiny.
Regulatory and Compliance Scrutiny
Just as crucial is the custodian's regulatory status. Partnering with an unlicensed or lightly regulated provider is an invitation for disaster and introduces massive counterparty risk. You have to be certain their compliance framework is not only robust but also perfectly aligned with your firm’s own legal and reporting duties.
The gold standard here is finding a qualified custodian, like a state- or federally-chartered trust company or bank. This isn't just a fancy title; it's often a legal necessity that signifies a much higher bar for regulatory oversight, capital requirements, and fiduciary responsibility. Make sure to verify their licenses and look into their history with agencies like the NYDFS or the OCC. You’ll also want to confirm they have a rock-solid, auditable KYC/AML program that actively uses blockchain analytics tools to screen for and block illicit funds.
Operational and Financial Stability
Finally, you need to look at the people, processes, and financial health behind the technology. The best tech and compliance in the world don't mean much if the provider can't support your day-to-day operations or if they’re on shaky financial ground. Ask tough questions about their service level agreements (SLAs) for customer support, their typical transaction processing times, and the reliability of their API.
Demand transparency on their financial health. This includes seeing their balance sheet and understanding the real scope of their insurance coverage. Don't just tick the "has insurance" box—get the details. Who is the underwriter? What are the actual coverage limits? And what specific scenarios, like internal theft or collusion, are explicitly covered? A true partner will be an open book about their operational resilience and financial stability, giving you the confidence you need for a long-term relationship.
Institutional Custody Provider Evaluation Checklist
Choosing a custody partner requires a structured and thorough evaluation. The following checklist provides a framework for asking the right questions across the most critical areas, ensuring you cover all your bases before making a commitment.
| Evaluation Category | Key Questions to Ask |
|---|---|
| Security & Technology | What is your exact key management architecture (MPC, HSM, hybrid)? What percentage of assets are held in cold storage? Can you provide recent SOC 1/SOC 2 reports and penetration test results? |
| Regulatory & Compliance | Are you a regulated trust company or bank (i.e., a qualified custodian)? Which jurisdictions are you licensed in? Can you describe your KYC/AML and transaction monitoring processes? |
| Insurance Coverage | What is the total limit of your insurance policy? Who is the underwriter? Does the policy cover both internal and external theft, including collusion? Is there a co-insurance requirement? |
| Operational Support | What are your SLAs for customer support and transaction finality? What are the procedures for onboarding new assets or whitelisting addresses? Can you provide API documentation and uptime statistics? |
| Financial Viability | Are you willing to share your company's balance sheet or audited financials? Are client assets held in a bankruptcy-remote legal structure? |
| Counterparty Risk | Are client assets fully segregated from your own corporate assets? How do you manage risks associated with sub-custodians or other third-party dependencies? |
By systematically working through this checklist, you can move beyond marketing pitches and make an informed decision based on verifiable facts and a clear understanding of the risks involved. This diligence is the cornerstone of a secure and successful institutional crypto strategy.
A Few Common Questions
Diving into the world of institutional crypto custody often brings up some very specific questions. Let's tackle a few of the most common ones to clear up the details around the technology, regulations, and what's possible in practice.
Think of this as a quick-reference guide to help you build a more solid, practical understanding of how this specialized corner of the financial world really works.
What’s the Difference Between a Qualified and Non-Qualified Crypto Custodian?
The real difference comes down to regulation and legal responsibility. A qualified custodian isn't just any company; it's a regulated financial institution, like a bank or a trust company, that has to meet tough legal and capital requirements set by agencies like the SEC. For many investment funds, using one is a legal must-have to protect their investors.
A non-qualified custodian might offer great security, but they don't have that official regulatory stamp of approval. This is a deal-breaker for most institutional players who have a fiduciary duty to work only with providers that meet the highest legal and operational benchmarks.
How Does MPC Technology Actually Make Custody Safer?
Multi-Party Computation (MPC) is a game-changer because it eliminates the single greatest point of failure in crypto: the private key. Instead of having a complete key sitting in one place (a hacker's dream), MPC technology mathematically shatters it into encrypted pieces, or "shards." These shards are then stored and managed in completely separate locations.
When it's time to sign a transaction, the shards work together to create the signature without ever being pieced back together. This means a thief would have to breach multiple, independent systems at the exact same time to get anywhere—a monumentally difficult task.
MPC flips the script on key management. You're no longer defending a single vault but a distributed, resilient network. It’s a core innovation that makes institutional-grade custody possible.
Can Institutions Put Custodied Assets to Work in Staking or DeFi?
Yes, absolutely. The days of custodians just offering a digital vault are over. Top-tier providers now have integrated platforms that let their clients stake assets to earn yield or interact with DeFi protocols, all from within their secure custody environment.
These aren't just add-ons; they are purpose-built services. They're designed to give institutions a secure bridge to on-chain opportunities without sacrificing the strict security and compliance controls they depend on. It’s how institutional capital can be both safe and productive in the digital asset world.
At Stablecoin Insider, we provide the in-depth analysis you need to stay ahead in the world of digital assets. Explore our expert articles and reports to master the complexities of stablecoins, custody, and decentralized finance. Learn more at https://stablecoininsider.com.






