Table of Contents
Think of crypto cross-chain bridges as the essential connectors of the decentralized world. They are the digital infrastructure that allows completely separate blockchains to talk to each other, share information, and move assets back and forth.
Why Blockchains Need Bridges to Connect
Picture each blockchain—Bitcoin, Ethereum, Solana—as its own self-contained digital island. Each one has a unique culture, a native currency, and a distinct set of rules. They’re powerful and vibrant on their own, but they're also completely isolated. Value gets trapped, and innovation is confined within their digital shores.
This isolation is one of the biggest hurdles in crypto. If these digital economies can't connect, you can't use your Bitcoin in an Ethereum DeFi app, and a developer can't build a project that pulls liquidity from multiple networks at once. This fragmentation creates digital silos, slowing down the growth of the entire ecosystem.
Crypto cross-chain bridges are the solution. They are the shipping lanes and flight paths that finally connect these blockchain islands. When you use a bridge, you can send an asset from one chain to another, helping to create a more fluid and interconnected digital economy. This opens up a world of new possibilities.
The Power of Interconnectivity
Bridges are paving the way for a more unified and efficient Web3. They enable a smooth experience where assets and data can flow freely, sparking more collaboration and unlocking new use cases across the board.
This connectivity is critical for a few key reasons:
- Better Capital Efficiency: You can move your assets to wherever they work hardest for you—chasing better yield farming opportunities or simply finding lower transaction fees without the hassle of selling and rebuying.
- More Powerful dApps: Developers can get creative, building applications that combine the strengths of different blockchains. Imagine pairing Ethereum's rock-solid security with the lightning-fast speed of a Layer 2 network.
- A Simpler User Experience: Life gets easier for users. Instead of juggling a dozen wallets for different networks, you can manage your assets more holistically.
This space is growing at a staggering pace. The blockchain bridge market was valued at around $3.1 billion in 2024 and is on track to hit an estimated $25 billion by 2035. For a closer look at these numbers, check out the latest market analysis.
At their core, these bridges employ a messaging system that permits blockchains to pass information to each other in a verifiable way. This ensures that data and assets can move seamlessly across disparate networks.
Crafting this kind of foundational interoperability is a job for a skilled Blockchain Solutions Architect. It's their vision that turns a collection of isolated digital islands into a powerful, interconnected ecosystem. As we dive deeper, you'll see just how this vision is being brought to life.
How a Cross-Chain Bridge Transaction Works
It’s easy to think of a cross-chain bridge as some kind of crypto teleporter, but that’s not quite right. A better way to picture it is as a sophisticated escrow service. When you send assets across a bridge, you’re not actually moving your original tokens. Instead, you're locking them up on one blockchain and creating a perfectly backed, redeemable version on another.
The most common way this happens is through a lock-and-mint mechanism. Think of it like this: you have US dollars but need to spend money in Europe. You could deposit your dollars into a secure vault, and in exchange, you'd get an equal amount of "tokenized" euros. These aren't real euros, but they're fully backed by your dollars and spendable in the European economy.
That’s exactly what happens in a typical bridge transaction. You lock your original asset—say, ETH on Ethereum—into a smart contract. That triggers a message to the destination chain, like Solana. Once that message is confirmed, the bridge’s smart contract on Solana mints a brand-new "wrapped" token (like wETH) of the exact same value. Suddenly, you have a key to unlock the entire Solana ecosystem.
Key Components of a Cross-Chain Bridge
This whole process doesn't happen on its own. It's a carefully coordinated effort between several key components, each with a specific job to ensure the transaction is secure and accurate from start to finish.
Here's a breakdown of the essential moving parts that make a bridge function.
| Component | Role | Analogy |
|---|---|---|
| Validators/Oracles | The independent observers. They watch the source chain for lock events and verify that the user deposited funds. | A notary public verifying a transaction. |
| Relayers | The messengers. They take the verified proof from the validators and deliver it to the destination chain's contract. | A trusted courier delivering a message. |
| Smart Contracts | The automated vaults and minting machines. They lock, mint, burn, and unlock assets based on verified messages. | An automated bank vault and currency press. |
Together, these actors form a trust system that allows value to flow between otherwise disconnected blockchain environments.
This infographic really drives home how bridges are creating a connected future by linking what were once isolated networks.
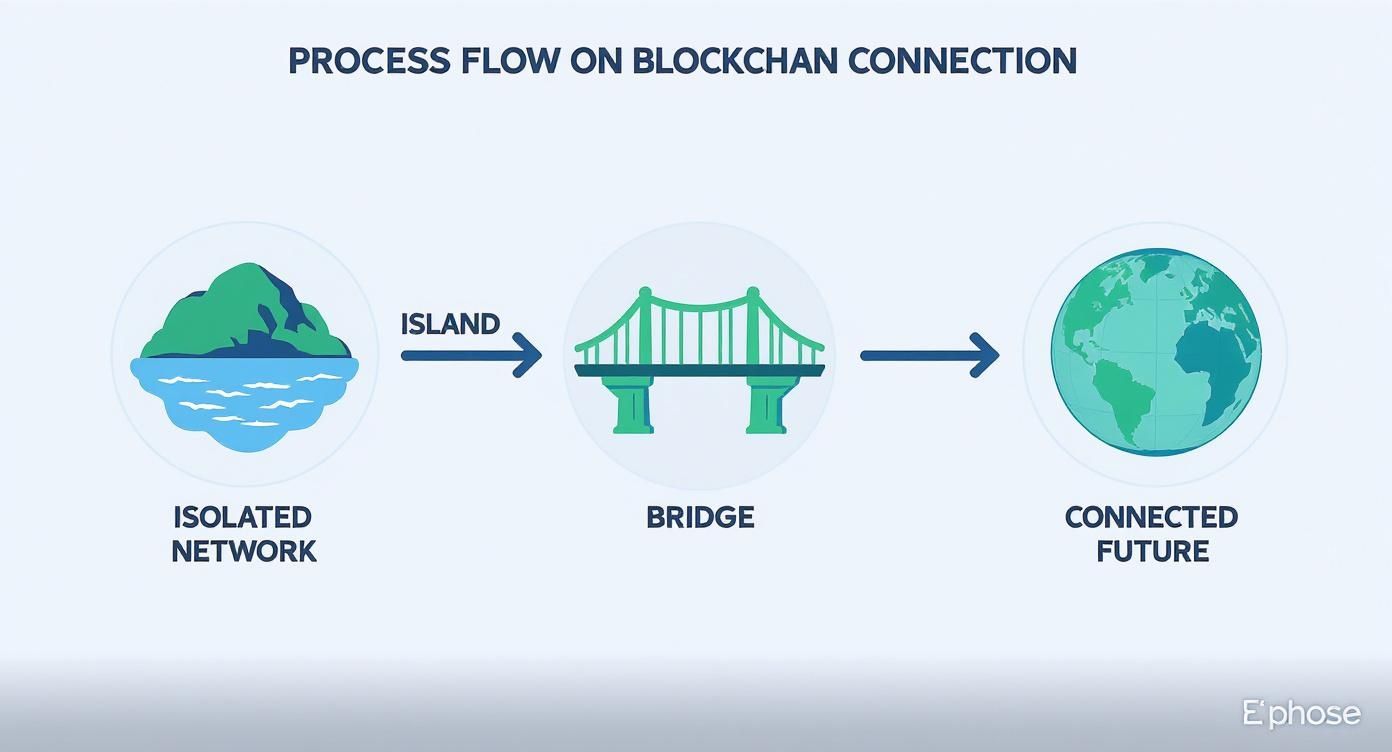
It’s a powerful visual for understanding the shift from a fragmented crypto space to a single, interconnected global network.
Completing the Round Trip
Okay, so what about when you want your original ETH back? The process just runs in reverse through a burn-and-unlock mechanism. You take your wrapped asset (the wETH on Solana) and send it to the bridge’s smart contract on that chain.
That contract "burns" the token, destroying it and taking it out of circulation for good. This burn event kicks off another message back to the source chain—Ethereum. Once that message is received and verified, the original smart contract unlocks your ETH and sends it right back to your wallet.
This intricate dance of locking, minting, burning, and unlocking is crucial. It guarantees that the total supply of the asset stays consistent across both chains, maintaining a perfect 1:1 peg. For every wrapped token that exists, there's a real, original asset locked away in a smart contract.
This system is what prevents the creation of "phantom" assets and keeps the entire process economically sound. Some protocols have even built unique messaging systems to make this communication more efficient. LayerZero is a great example, and you can learn more by reading this full review of the LayerZero bridge protocol. Getting a handle on these mechanics is the first step toward using cross-chain bridges with confidence.
Trusted vs. Trust-Minimized Bridge Designs
Not all crypto cross-chain bridges are built the same. When you look under the hood, they really split into two main camps based on one simple but critical question: who do you have to trust? This fork in the road gives us two distinct designs—trusted and trust-minimized bridges—and each comes with its own set of trade-offs in security, speed, and decentralization.

Getting a handle on this difference is everything when it comes to evaluating the risk of moving your assets. The core ideas behind bridge design often echo the way crypto wallets work, so understanding custodial and non-custodial approaches will give you a great head start.
Trusted Bridges: The Centralized Tollbooth
Think of a trusted bridge as a centralized tollbooth on a highway. It relies on a specific company or a small, known group of operators to check your transaction and hold onto your locked assets. When you send tokens across a trusted bridge, you're essentially putting your faith in these operators to be honest and secure.
Most of these designs use a multi-signature (multisig) wallet or a "federated" group of validators who all have to sign off on a transaction. It’s a convenient and often faster setup, but it also creates a glaring central point of failure.
- How they work: You send your crypto to an address controlled by the bridge operators. They confirm your deposit on their end and then mint the equivalent wrapped token for you on the other chain.
- Key characteristic: The safety of your money boils down to the integrity and security of a third party.
This model, with its reliance on a small group, makes it a juicy target for hackers. If they can compromise just a few keyholders, the entire pool of assets is at risk.
Trust-Minimized Bridges: The Automated Customs System
On the other side of the spectrum, trust-minimized bridges are engineered to slash—or completely remove—the need to trust a central operator. Picture an automated, decentralized customs system that runs on code, math, and clever economic incentives to keep things secure.
Instead of trusting people, you're trusting the open-source code and the cryptographic logic of smart contracts. This lines up perfectly with the whole ethos of decentralization by getting rid of those single points of failure.
Key Takeaway: The goal of a trust-minimized bridge isn't zero trust, but distributed trust. You’re placing your confidence in the code's integrity and the network's economic security, not a handful of intermediaries.
These bridges pull this off using more advanced tech. Two of the most common methods are:
- Light Clients: These bridges run a "light client"—a stripped-down version of a blockchain's software—right on the other chain. This allows them to independently verify transaction data cryptographically, without needing to ask a validator if it’s legit.
- Optimistic Rollups: This model works on an "innocent until proven guilty" basis. It assumes all transactions are valid upfront and gives anyone a "challenge period" to step in and submit proof of fraud if they spot something shady. The economic incentives are designed to make honesty the most profitable strategy.
Comparing Bridge Architectures
So which one is better? It’s not that simple. Choosing between these designs is a direct trade-off between security, speed, and cost. There's no one-size-fits-all answer; it all comes down to the specific use case and your personal risk tolerance. To see how this plays out in the real world, check out our detailed look at the best crypto cross-chain bridges in 2025.
Here’s a quick breakdown of the critical differences:
| Feature | Trusted Bridges | Trust-Minimized Bridges |
|---|---|---|
| Security Model | Relies on the honesty of a central operator or federation. | Relies on cryptographic proofs, smart contracts, and code. |
| Centralization | High, creating a single point of failure. | Low, distributing security across the network. |
| Speed | Often faster due to centralized processing. | Can be slower due to complex verification or challenge periods. |
| Cost | Typically lower transaction fees. | Can be more expensive due to on-chain verification costs. |
| Primary Risk | Counterparty risk (operator theft or compromise). | Smart contract risk (bugs or exploits in the code). |
Ultimately, the entire field of cross-chain bridges is on a quest to minimize trust while cranking up efficiency. Trusted bridges offer a straightforward user experience that’s hard to beat, but the industry is clearly shifting toward trust-minimized solutions that offer stronger security guarantees for the decentralized future of Web3.
Understanding the Bridge Security Trilemma
https://www.youtube.com/embed/tAlRmKHRXPg
When it comes to building crypto bridges, engineers are constantly wrestling with a tricky balancing act known as the security trilemma. It’s a foundational concept that says you can't have it all—a bridge simply can't be perfectly secure, universally connected, and lightning-fast at the same time. Every single bridge design is a series of calculated trade-offs.
Think of it like picking a vehicle. A race car is built for pure speed but it’s not practical for a family road trip. A massive freight truck can haul anything you want, but it’s never going to win a drag race. Bridge architects face the exact same problem: they have to choose which corner of the trilemma triangle to prioritize, and those choices directly impact every user.
Getting a handle on this trilemma is crucial because it defines the risks and rewards you face with every cross-chain transaction you make.
Navigating the Three Pillars
Each point of the trilemma is a core goal for any bridge, but pushing for one often means you have to give something up on another. Let's break down what each pillar really means and how these trade-offs play out in the real world.
- Security: At its core, this is about keeping user funds safe from hackers and glitches. A highly secure bridge relies on bulletproof cryptographic verification and tries to minimize trust in any single third party. This makes it incredibly tough to exploit.
- Generalizability: This is all about connectivity. How many different blockchains can the bridge talk to? A bridge with high generalizability can link totally different ecosystems, like connecting Ethereum to Solana, Cosmos, and beyond, no matter their underlying code.
- Speed: This one's simple: how fast does your transaction go through? The quicker you can access your assets on the new chain, the better the user experience, especially if you're trying to jump on a time-sensitive DeFi opportunity.
The problem is, these goals are often at odds. For instance, achieving Fort Knox-level security might require a ton of on-chain verification steps, which can seriously slow down transaction times and might only work between chains that are built similarly.
The Real-World Consequences of Trade-Offs
The design choices developers make aren't just theoretical; they have very real consequences. For example, crypto cross-chain bridges in 2025 are still grappling with this fundamental security-speed-generalizability puzzle, and no one has completely solved it. The most secure options, like the Inter-Blockchain Communication (IBC) protocol, are mostly stuck within the Cosmos ecosystem because they require all connected chains to share a compatible design.
On the flip side, you have bridges like Across Protocol, which prioritize speed. They use an optimistic model to get transfers done in under a minute, but this introduces a new risk: you have to trust that their relayers are acting honestly. For more on this, check out the great analysis in the a16z crypto report.
The Wormhole Exploit: A Case Study in Security Trade-Offs
One of the most painful lessons in bridge security came from the $325 million Wormhole exploit. The bridge was designed for speed and broad connectivity between giants like Ethereum and Solana, but it had a critical bug in its smart contract. Attackers found that flaw and used it to mint 120,000 "wrapped" ETH on Solana without ever locking up the real ETH on Ethereum, completely draining the bridge's reserves.
That incident was a massive wake-up call for the entire industry. It proved that chasing speed and connectivity without obsessive attention to security audits and solid engineering can lead to catastrophic failure.
Making an Informed Choice
As a user, understanding the trilemma gives you the power to choose the right tool for the job.
Are you moving a large sum of money where top-tier security is the only thing that matters, even if it’s slow? Or are you just trying a low-risk DeFi strategy where getting the transaction done quickly is more important?
There’s no single "best" bridge—only the best one for what you need to do right now. Some are built like armored trucks: slow and steady, but incredibly safe. Others are more like sports cars: fast and agile, but with less protection. The key is to understand the trade-offs of the crypto cross-chain bridge you're using and be comfortable with the risks that come with it. As you explore your options, it's also worth thinking about how different assets perform when bridged; you can learn more about the nuances of stablecoin bridging in 2025 for a deeper look.
How Bridges Shape DeFi and Capital Flow
Think of cross-chain bridges as the vital arteries of the Decentralized Finance (DeFi) economy. They're not just a piece of tech; they're the conduits that let capital flow from mature, high-liquidity ecosystems like Ethereum into promising new chains. This movement of money is what fuels genuine competition and innovation across Web3.
Without bridges, it would be like your investment capital being trapped in one country's stock market. Bridges tear down those digital borders, letting you send assets to wherever they can find the best returns. This isn't some niche activity anymore—it's a core strategy for serious DeFi users.
The Great Migration of Liquidity
This flow of capital isn't happening by accident. It's a calculated hunt for better opportunities. Users are constantly shifting funds between chains to find more favorable financial conditions, creating a market that’s incredibly dynamic and competitive.
So, why are people moving their assets around so much?
- Chasing Higher Yields: A new blockchain might roll out a decentralized exchange with temporarily massive rewards to attract liquidity. Bridges are the on-ramp for users to jump in and capitalize on those yield farming opportunities.
- Finding Lower Borrowing Rates: Just like in the real world, borrowing costs aren't the same everywhere. A user might bridge their assets to a network with a less crowded lending protocol to get a loan on much better terms.
- Accessing a Wider Universe of dApps: Some of the most exciting new games, NFT marketplaces, and DeFi tools are being built on newer, faster chains. Bridges are the ticket in, letting you interact with platforms you’d otherwise be locked out of.
This constant movement shows how much the market has matured. Capital is no longer siloed within a single ecosystem. It's fluid, always seeking efficiency and rewarding the most compelling projects, no matter which blockchain they're built on. We dive much deeper into this in our detailed guide on cross-chain DeFi strategies.
Following the Money Trail
The transaction data tells the whole story. In 2025, cross-chain bridges are processing staggering volumes, with total cross-chain activity hitting $56.1 billion in July alone. Ethereum is still the main source of all this liquidity. Its net inflows hit around $10.1 billion year-to-date in 2025—a figure almost eight times larger than the next closest blockchain. For anyone who loves data, you can find more insights about cross-chain capital flows on MEXC.
The numbers are clear: while new chains are definitely attracting capital, Ethereum continues to operate as the foundational "central bank" of DeFi. Liquidity tends to start there before being bridged out to chase opportunities elsewhere.
At the end of the day, crypto cross-chain bridges are powerful economic engines, not just technical plumbing. By letting capital move without friction, they ensure the best ideas and most efficient platforms get the resources they need to thrive. This is the dynamic that pushes the entire DeFi space forward, building a more connected and resilient financial system for everyone.
A Practical Checklist for Using Bridges Safely

Crypto bridges open up a world of possibilities, but let's be honest: they're also a massive security headache. By design, they concentrate huge amounts of assets into a few smart contracts, painting a giant target on their backs for hackers. If you're going to navigate this space, you need more than just optimism—you need a healthy dose of caution and a solid process for checking things out.
Thinking about security first isn't just a good idea; it's the only way to protect your funds. This checklist gives you a practical framework to follow, breaking down what you absolutely must do before you even think about connecting your wallet.
Research the Bridge and Its History
Before you move a single dollar, your first job is to do some serious digging. A bridge's reputation and history tell you almost everything you need to know about its reliability and whether the team behind it actually cares about security.
Start with the project's track record. Has it ever been hacked? It happens. The real question is, how did the team react? Did they go silent, or were they transparent with users? Most importantly, did they make everyone whole who lost money? A team that handles a crisis with integrity is often more trustworthy than one that's never been tested.
Next, it’s time to look at the audits.
- Check for Audits: Has the bridge been audited by reputable security firms? If you don't recognize the auditor's name, that's a red flag.
- Read the Report: Don't just tick the box because an audit exists. Find the actual report. What vulnerabilities did the auditors find, and is there proof the team fixed them?
- Understand the Security Model: Figure out if you’re dealing with a trusted or trust-minimized bridge. This tells you where the risk lies—are you counting on a centralized operator to be honest, or are you worried about a smart contract bug?
Execute Your Transaction with Caution
Once you’ve done your homework and picked a bridge, the execution phase is where simple mistakes can cost you dearly. It’s not just about major hacks; protecting yourself from common scams and user error is just as important.
Always Start with a Test Transaction: Never, ever bridge your full amount on the first try. Send a small, insignificant amount first. Wait for it to show up safely in your destination wallet. This one step can save you from a total loss.
This simple habit protects you from typos, network issues, or other unexpected problems. Beyond that, make these practices second nature:
- Bookmark the Official Website: Phishing is everywhere. Scammers are experts at creating pixel-perfect fake sites to drain your wallet. Always use a bookmark you've saved yourself, never a link from a random tweet, Discord message, or search result.
- Double-Check the Contract Address: When you get your assets on the new chain, verify you have the correct contract address. Scammers love to deploy fake tokens with the same name to trick you into trading for a worthless asset.
- Understand Wrapped Asset Risks: Remember, the "wrapped" token you receive is just an IOU. Its value is completely tied to the security of the bridge holding the original. If that bridge gets hacked, your wrapped token could become worthless overnight. For a deeper dive into how this works with dollar-pegged assets, check out our guide on bridging stablecoins between major networks.
Your Cross-Chain Bridge Questions, Answered
If you're digging into cross-chain bridges, you've probably got questions about how they work, how safe they are, and what they cost. Let's break down some of the most common ones with clear, no-nonsense answers.
How Is a Bridge Different From an Exchange?
This is a great question because they can feel similar at first glance. Think of it this way: a centralized exchange (CEX) is like a currency exchange booth at an airport. You hand over your crypto to a company, they hold it for you, and they let you trade it for other assets within their own private system. You're trusting a middleman completely.
A cross-chain bridge, however, is more like a direct tunnel between two separate countries (blockchains). It's a tool that lets you move the same asset from one network to another, usually by creating a "wrapped" version on the other side. You're not trading your asset for something new; you're just teleporting its value across chains without handing custody over to a big company.
Are Crypto Cross-Chain Bridges Ever 100% Secure?
In a word: no. Nothing in software is ever truly 100% secure, and bridges are particularly complex beasts. They have multiple potential points of failure, from bugs hiding in smart contracts to the security of the validators or relayers that keep the bridge running.
The goal isn’t perfect, un-hackable security—that’s a myth. The real aim is to build increasingly resilient systems that minimize trust and reduce the number of ways things can go wrong.
The best bridges get hammered on by multiple independent security auditors and even run bug bounty programs, paying friendly hackers to find flaws before the bad guys do. Still, a risk always remains, which is why it's so important to be careful.
What Happens to My Assets If a Bridge Gets Hacked?
This is the scary part, and the answer depends on the bridge and the hack itself. When a hacker drains the real assets locked on the source chain, the wrapped tokens you're holding on the destination chain can suddenly become worthless. Their backing is gone.
In a few massive, high-profile hacks, the project's team or its big-name investors have stepped in to bail out users and make them whole. But this is the exception, not the rule. More often than not, users face a total loss of their funds with no way to get them back. This is exactly why you need to dig into a bridge's track record and security setup before trusting it with your money.
Why Are Transaction Fees So High on Some Bridges?
Bridge fees can definitely feel painful, and it comes down to a few things. First off, a single cross-chain transfer is actually two separate blockchain transactions: one to lock your asset on the source chain and another to mint the wrapped version on the destination chain. You have to pay the gas fees for both. If one of those chains is Ethereum during a busy period, that cost alone can be eye-watering.
On top of the network gas fees, the bridge protocol itself usually adds its own fee. This is used to pay the people or systems (relayers and validators) that secure the bridge and to cover the project's own operating costs. Sometimes, the more secure and decentralized a bridge is, the more complex its operations are, which can also translate to slightly higher fees.
At Stablecoin Insider, we provide in-depth analysis and guides to help you safely navigate the complexities of DeFi and digital assets. Explore our resources to stay informed about the latest in blockchain technology and stablecoins. Learn more at https://stablecoininsider.com.







